Reliable Safety Services to Secure Your Corporate Possessions
In today's quickly evolving service landscape, protecting business properties has become extra important than ever before. Reputable protection services are important to guarding important resources, delicate details, and the general wellness of an organization. With a raising number of physical and digital dangers, organizations need detailed safety options that guarantee their assets remain secured in any way times.
Our specialist security services offer a variety of innovative options customized to fulfill the unique needs of your corporate environment. From physical safety and security steps such as gain access to control systems and monitoring solutions to electronic hazard discovery and emergency situation feedback methods, we give an all natural strategy to guarding your properties.
Our committed group of safety and security experts is dedicated to providing reliable and reliable safety solutions that reduce threat and boost the general security of your organization. With our solutions, you can have tranquility of mind knowing that your corporate possessions are in capable hands.
Physical Protection Solutions
- Physical protection services are vital for safeguarding corporate properties and making sure the security of employees and delicate info. These solutions incorporate a series of innovations and measures designed to prevent unapproved access, burglary, vandalism, and various other risks to physical rooms.
One of the primary elements of physical protection is gain access to control systems (corporate security). These systems permit only authorized people to get in restricted locations, utilizing methods such as crucial cards, biometric scans, or PIN codes. By restricting access to delicate areas, services can mitigate the danger of burglary, sabotage, or unauthorized disclosure of private information
One more essential element of physical protection is monitoring. Closed-circuit tv (CCTV) video cameras are usually deployed throughout a facility to check activities and prevent potential trespassers. With developments in technology, video analytics and facial acknowledgment capabilities can enhance the efficiency of security systems, enabling real-time risk discovery and feedback.
Physical barriers, such as fences, entrances, and enhanced doors, additionally play an important function in securing company assets. These barriers act as deterrents and make it a lot more hard for unapproved individuals to acquire access. Furthermore, security system and movement sensing units can signal security personnel or legislation enforcement companies in the occasion of a violation or dubious task.
Digital Hazard Discovery
Digital Threat Detection is an important aspect of comprehensive security steps, using sophisticated modern technologies to recognize and minimize possible cyber hazards to company possessions. In today's electronic landscape, services face an enhancing number of innovative cyber strikes that can bring about considerable monetary losses and reputational damage. Digital Threat Detection intends to proactively react and determine to these threats before they can create damage.
To successfully find digital threats, companies use a variety of innovative technologies and strategies. These consist of intrusion discovery systems, which keep an eye on network web traffic for suspicious task, and malware analysis devices, which evaluate and recognize harmful software. In addition, behavioral analytics and artificial intelligence algorithms are utilized to find anomalies in customer behavior and recognize potential expert risks.
Digital Hazard Detection additionally involves real-time surveillance of network facilities and endpoints to respond and recognize to active dangers. Security operations facilities (SOCs) play a crucial function in this procedure, as they continuously check and analyze security informs to promptly discover and react to possible threats. Danger knowledge feeds are made use of to stay updated on the most current cyber dangers and susceptabilities.
Monitoring and Tracking Providers
To make certain thorough protection steps, companies can use security and surveillance services as a necessary element of guarding their company possessions. Monitoring and surveillance services supply real-time monitoring and analysis of tasks within and around the organization, allowing prompt recognition and action to possible protection dangers.
By read the article making use of innovative monitoring modern technologies such as CCTV electronic cameras, activity sensing units, and gain access to control systems, organizations can efficiently monitor their premises and discover any type of unauthorized access or dubious tasks. This positive method serves as a deterrent to potential crooks and helps keep a safe and secure setting for workers, visitors, and valuable properties.
In enhancement to physical monitoring, organizations can additionally take advantage of digital surveillance solutions. These services involve the surveillance of digital networks, systems, and devices to recognize any type of malicious or uncommon activities that might compromise the security of company data and delicate info. Through continual tracking and evaluation of network web traffic and system logs, possible safety breaches can be identified early, enabling immediate therapeutic action.

Access Control Solution
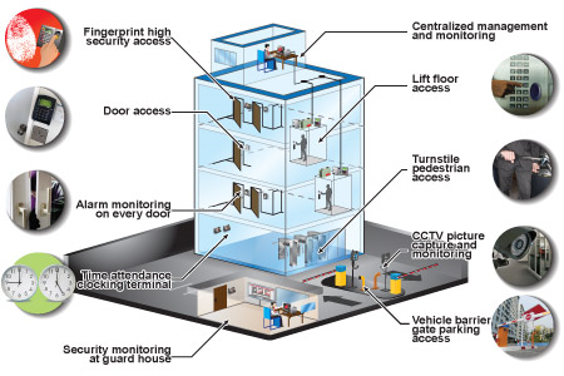
These systems utilize different modern technologies such as key cards, biometric scanners, and PIN codes to reject or provide accessibility to individuals. By implementing gain access to control systems, business can successfully limit and take care of access to vital locations, lessening the threat of unapproved access and possible burglary or damages to beneficial assets.
Among the key benefits of access control systems is the ability to track and keep track of the movement of people within a facility. This function enables organizations to generate detailed reports on that accessed details locations and at what time, supplying useful data for safety and security audits and investigations.
Additionally, gain access to control systems can be integrated with various other protection procedures, such as monitoring video cameras and alarm, to boost general safety and security. In case of a safety breach or unapproved gain access to attempt, these systems can trigger prompt informs, allowing swift feedback and resolution.
Emergency Response and Case Administration
In the realm of comprehensive safety actions, the focus currently shifts to the critical facet of efficiently taking care of emergency response and occurrence management in order to guard business properties. Trigger and reliable action to incidents and emergency situations is essential for decreasing potential losses explanation and securing the well-being of workers and stakeholders.
Emergency situation action and case administration entail a methodical approach to managing unforeseen events and disturbances. This consists of developing durable strategies and protocols, training workers, and collaborating with relevant authorities. By developing clear lines of communication and marked emergency action groups, companies can guarantee a swift and collaborated feedback when faced with emergencies such as fires, natural catastrophes, or protection breaches.
Incident monitoring goes past instant emergencies and encompasses the administration of any kind of unplanned events that may interfere with regular company operations. This might include occasions such as power failures, IT system failures, or supply chain interruptions. Reliable case management involves immediately examining the scenario, implementing necessary steps to reduce the effect, and bring back typical procedures as promptly as feasible.
Verdict
To conclude, dependable safety and security services play a vital duty in guarding company properties. By carrying out physical protection options, electronic threat detection, surveillance and monitoring solutions, gain access to control systems, and emergency response and incident monitoring, services can reduce risks and shield their useful resources. These services give a durable defense against possible risks, ensuring the safety and security and stability of corporate properties.
One of the main components of physical protection is gain access to control systems.Digital Threat Discovery is a vital element of thorough safety steps, making use of sophisticated modern technologies to determine and mitigate prospective cyber threats to company assets. Safety operations facilities (SOCs) play a crucial function in this process, as they constantly monitor and examine security notifies to promptly discover and react to possible risks.Proceeding the conversation on extensive security steps, accessibility control systems play an important role in making sure the guarding of business assets. By carrying out physical protection options, electronic threat surveillance, security and discovery solutions, access control systems, and emergency reaction and occurrence administration, organizations can minimize threats and protect their valuable resources.